Hacking with the Bookeen Cybook Orizon Tear down and Serial connection
Let's connect via Serial to this device, setup the wireless card, and enable an ssh server on it.
Connecting SIO
The serial connection is on the debug connector JA901 at the bottom left of the board :

Pinout is (right to left with the battery on bottom) :
| Pin | Usage |
|---|---|
| 1 TX1 | UNUSED |
| 2 RX1 | UNUSED |
| 3 TX0 | SERIAL TX |
| 4 RX0 | SERIAL RX |
| 5 TX3 | UNUSED |
| 6 RX3 | UNUSED |
| 7-13 | ? |
| 14-16 GND | SERIAL GND |
| 16-18 VDD | SERIAL VCC (3.3V) |
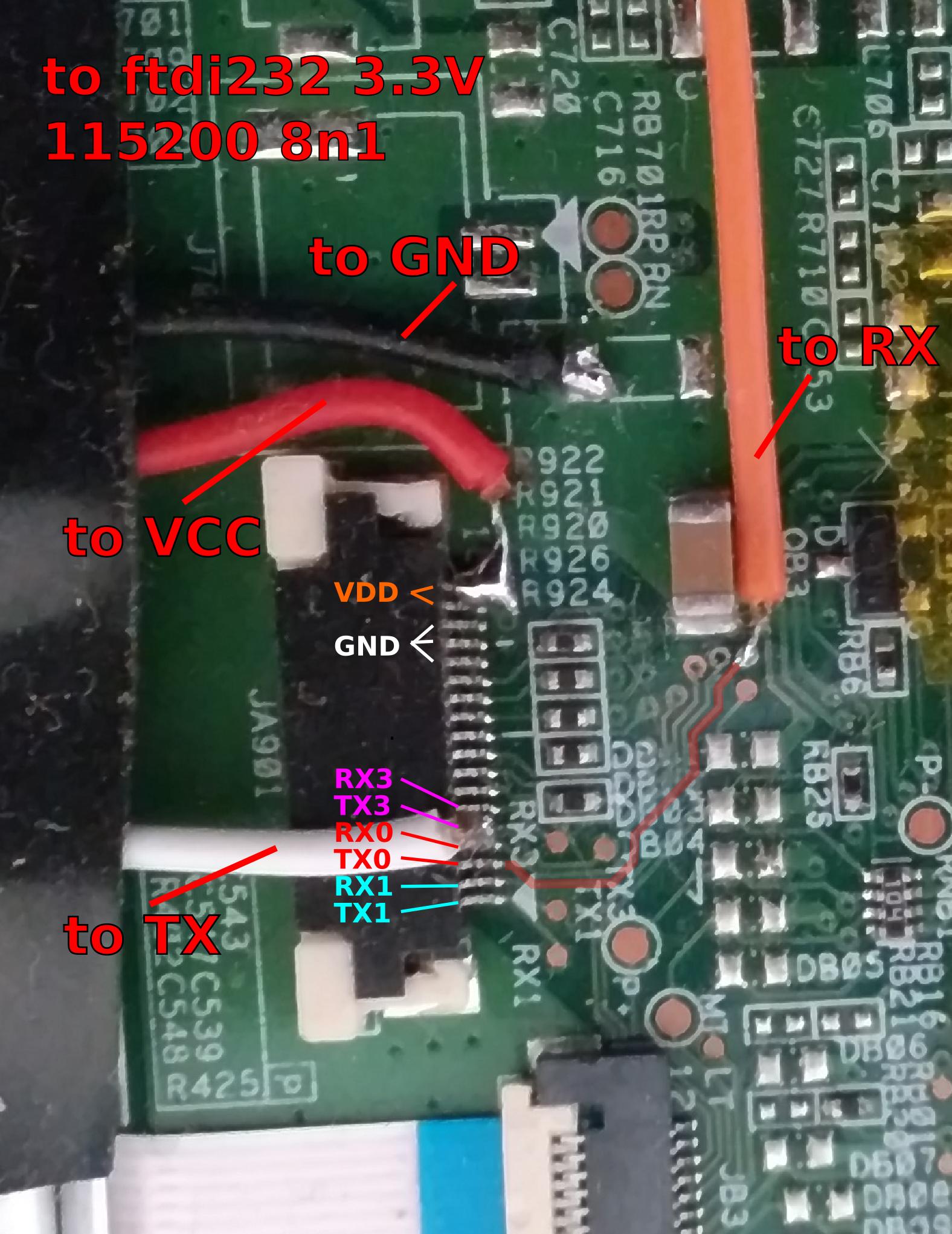
You can then use minicom to login :
sudo minicom -b 115200 -D /dev/ttyUSB0Login : root
FnX Bootloader for s3c2416 build on confucius version master_6376fd19638ef062_b360
Build time "Mon, 11 Oct 2010 14:15:38 +0200"
Copyright (C) 2010 Bookeen
Detected: Bookeen Cybook Orizon, A00/A01/A022;FnX - Bookeen Cybook Orizon - Terminal
Battery level: [==================================== ]
Info: Battery condition reasonable
Info: Reset/boot due to Software reset I0: 00000000...
Starting: Uncompressing Linux..........................................................................
***: Cybook Linux Starting...
***: Prepare filesystem...
***: Does software want to update? No
***: Check if user want to update...
***: Verify partitions...
fsck 1.41.9 (22-Aug-2009)
rootfs: clean, 1177/38456 files, 120508/153600 blocks
boot: clean, 15/3840 files, 9958/15360 blocks (check deferred; on battery)
privatefs: recovering journal
privatefs: clean, 66/2560 files, 1516/10240 blocks (check deferred; on battery)
***: Continue booting.....
***: Doing critical nasty things......
***: Starting BooReader...
Welcome to your Cybook Orizon!
CybookOrizon login: root
login[872]: root login on 'ttySAC0'
[root@CybookOrizon ~]#Keep the device awake
You need to either power the device via micro USB, or kill processes ebrmain and boordr :
pkill ebrmain
pkill boordr Wifi connection
Firmware loading
You can load the wifi firmware and enable the wifi interface (which will apear as 'eth0') with the init script that's in /etc/init.d :
/etc/init.d/wireless start
[root@CybookOrizon ~]# ifconfig
eth0 Link encap:Ethernet HWaddr 00:27:13:F7:E3:F7
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:58 (58.0 B) TX bytes:0 (0.0 B) Connecting to a network
You can use iwlist scan to search for your network, which you can then connect to using wpa_supplicant.
Edit /etc/network/interfaces and add the following lines :
auto eth0
iface eth0 inet dhcpCreate the file /etc/wpa_supplicant.conf that should contain :
network={
ssid="yourSSID"
psk="yourPSK"
}Then run wpa_supplicant -Dwext -ieth0 -c/etc/wpa_supplicant.conf & and once connected, use the network init script :
/etc/init.d/network startYou should now be connected to your Wireless AP.
SSH connection
By default the root account has no password, so you should change it in order to be able to connect via SSH :
passwd # then type your password two timesFinally, you can start the dropbear ssh server with /etc/init.d/dropbear start.
As this is quite an old version of dropbear, the generating utility dropbearkey only comes with rsa/dss, and the only available key exchange algorithm is SHA-1, which was disabled in openssh 8.8.
If you plan on using an ssh key to login, you'll have to re-enable those algorithms :
ssh -o KexAlgorithms=diffie-hellman-group1-sha1 -o HostkeyAlgorithms=ssh-rsa -i .ssh/bookeen_rsa_key root@10.10.10.10Have fun :)
CPU info
cat /proc/cpuinfo
Processor : ARM926EJ-S rev 5 (v5l)
BogoMIPS : 199.47
Features : swp half thumb fastmult edsp java
CPU implementer : 0x41
CPU architecture: 5TEJ
CPU variant : 0x0
CPU part : 0x926
CPU revision : 5
Cache type : write-back
Cache clean : cp15 c7 ops
Cache lockdown : format C
Cache format : Harvard
I size : 16384
I assoc : 4
I line length : 32
I sets : 128
D size : 16384
D assoc : 4
D line length : 32
D sets : 128
Hardware : Cybook Orizon
Revision : 0100
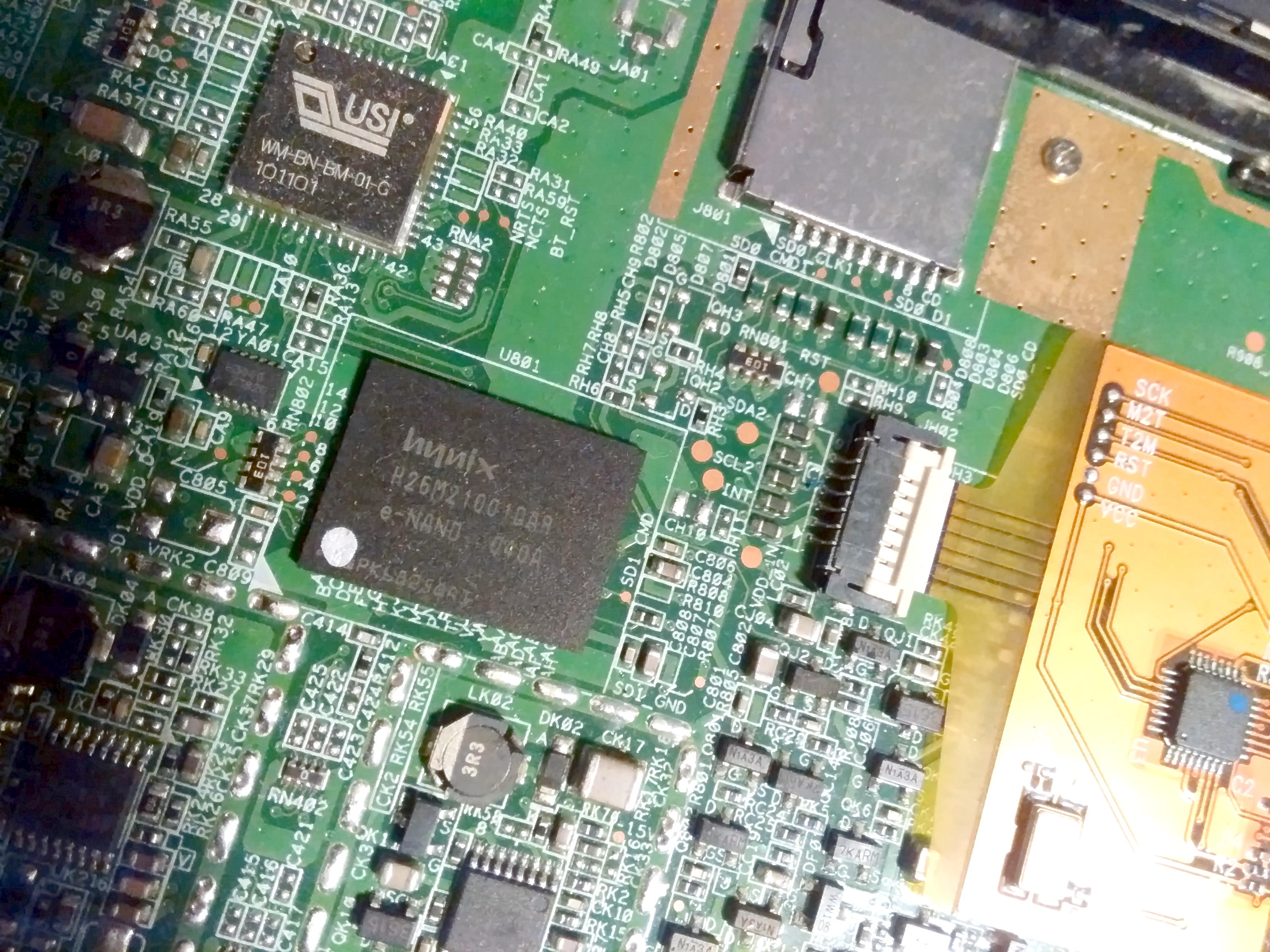
Serial : 0000000000000000Hardware components
SOC : S3C2416
Screen: Sipix AUO 6" 800x600 A0608E02
Display controller : AUO K-1900
Video DRAM : Etron Tech EM686165VE-7H
Wifi/Bluetooth : USI WM-BN-BM-01-0
Storage : Hynnix H26M210010AR e-NAND 2GB Flash
Memory : 32MB
CPU : 200 Mhz
Misc
bootsplash screen
The boot splash picture is in /boot/ and is a 600x800 greyscale, indexed 16 colors bmp file (filesize 240,1 KB).
If using gimp to edit it, make sure to check the compatibility option "Do not write colorspace information".
Then, to replace it, you first have to mount /boot as rw ;
mount /boot
mount -o remount,rw /bootthen edit your boot splash pic, and put it on the device as /boot/bootsplash.bmp via ssh:
scp bootsplash.bmp CybookOrizonIP:/boot/
Screensaver and thumbnail file formats
The file format is t4b, and you can find some scripts to convert from an to this format here :
https://github.com/ABelliqueux/t4b-tools
The default screen saver pictures are in /mnt/app/res/ds.
Most UI assets are in /mnt/app/res/img.
Wifi + SSH at boot
In order to enable Wireless, connect to your AP and start the SSH server automatically at boot, you can create a script in /etc/init.d with this content :
# Start ALL the things !
#
case "$1" in
start)
echo "Killing useless processes..."
pkill ebrmain
pkill boordr
echo "Enabling wireless"
/etc/init.d/wireless start
echo "Connecting to AP..."
wpa_supplicant -B -Dwext -ieth0 -c/etc/wpa_supplicant.conf
sleep 3
echo "Init network"
/etc/init.d/network stop
/etc/init.d/network start
echo "Starting SSH..."
/etc/init.d/dropbear start
;;
stop)
echo -n "Stopping all the things !"
/etc/init.d/dropbear stop
/etc/init.d/network stop
/etc/init.d/wireless stop
;;
restart|reload)
"$0" stop
"$0" start
;;
*)
echo $"Usage: $0 {start|stop|restart}"
exit 1
esac
exit $?Make sure the script has the right owner/permissions :
chmod 755 /etc/init.d/*
chown default:default /etc/init.d/*Then, remove/backup the existing symlinks in /etc/rc.d :
rm /etc/rc.d/*and create a new one to your script :
ln -s /etc/init.d/custom /etc/rc.d/S05customInput
The Cybook's physical buttons (up, left, down, right, middle and on/off/sleep) can be accessed from /dev/cyio
Pressing a button triggers the following packets :
| Button | Packet content HEX | ASCII |
|---|---|---|
| Left | 6B 80 10 6C | l |
| Up | 6B 80 10 75 | u |
| Right | 6B 80 10 72 | r |
| Down | 6B 80 10 64 | d |
| Center | 6B 80 10 65 | e |
| Sleep | 6B 80 10 6F | o |

Pictures










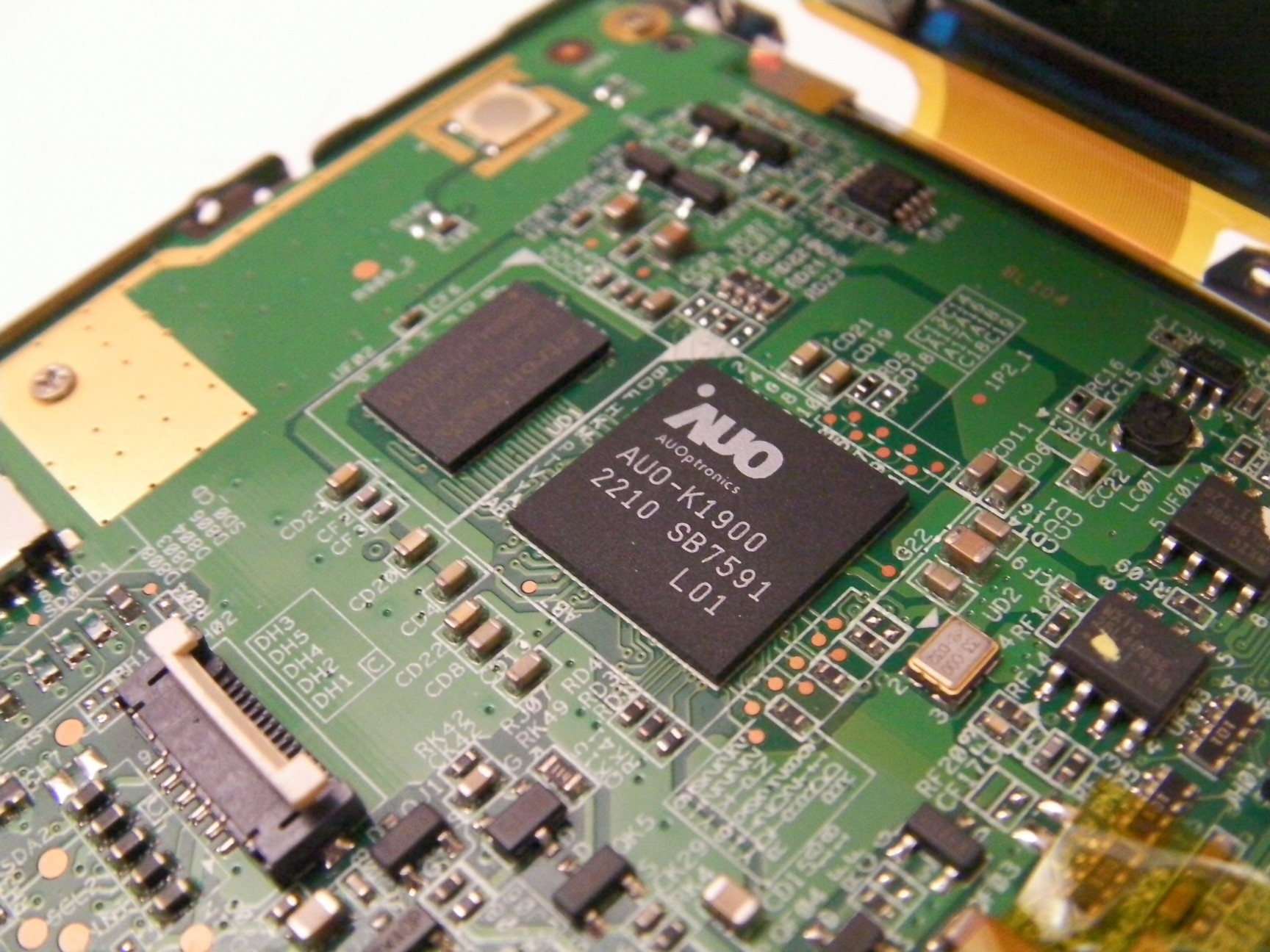
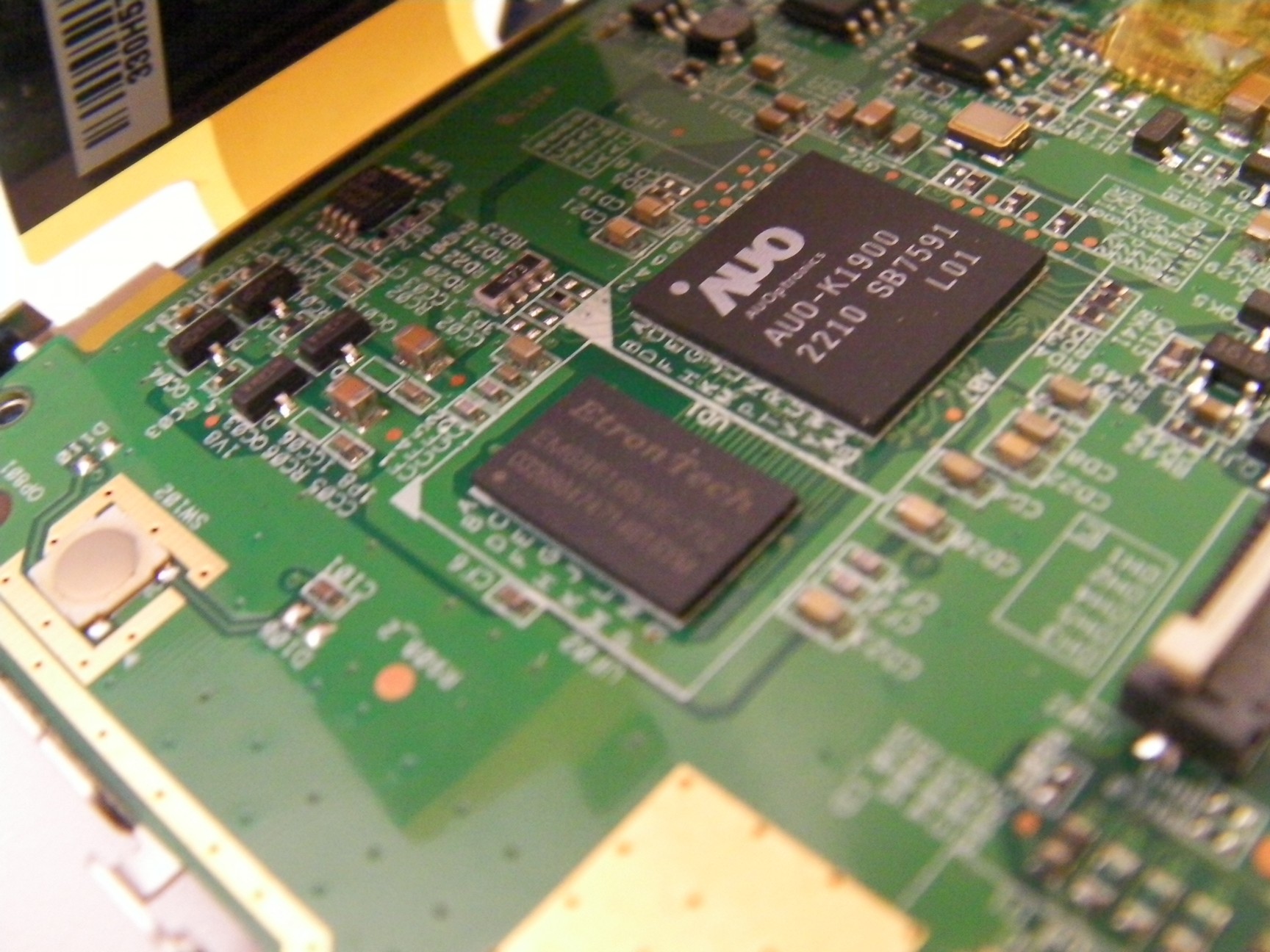

Links
http://wiki.mobileread.com/wiki/Cybook_Orizon
https://www.e-ink-info.com/why-did-bookeen-use-sipix-and-not-e-ink-their-upcoming-orizon-reader
https://web.archive.org/web/20101203015220/http://www.fwma.de/pmwiki/pmwiki.php?n=Main.OYO
https://shkspr.mobi/blog/2013/04/disassembling-an-ereader/
https://wiki.techinc.nl/OYO_Hacking
https://web.archive.org/web/20141218033547/http://ownyo.de/
https://p2k.unkris.ac.id/IT/2-3065-2962/Qisda-ES900_21112_p2k-unkris.html